Back in June 2024, CSO Online published an article titled "9 Ways CSOs Lose Their Jobs". The author opened the article with:
For top IT security execs, losing your job is remarkably easy. All it takes is a stupid decision, a simple oversight, or poor communication.
From that opening sentence, I knew X-Analytics would be at least a partial solution to a few of the 9 ways. Surprisingly, I did not expect that X-Analytics would help with all 9 ways.
According to the article, here are the 9 ways:
Overconfidence
Promoting Runway Complexity
Shortchanging GRC
Failing to Align Cybersecurity with Enterprise Objectives
Underemphasizing Access Controls
Ignoring the Human Factor
Allowing Abandoned Data to Linger
Not Building a Bridge to the Business
Complacency
Even if you disagree with the list, you have to admit there is relevance to the theme. Being a CSO is a tough job. You run a cost center that few people understand, you seldom get credit for the great things you accomplish, and you get blamed if something goes wrong for a problem that you partially own.
As a CSO, you need all the help you can get...especially if that help comes at a very reasonable price.
What is X-Analytics?
X-Analytics is a cloud-based cyber risk management application. With X-Analytics, you can create and manage your cyber risk profile. After creating your first profile and after each profile update, X-Analytics automatically determines your cyber risk condition, the benefit of your risk management strategy (including mitigation and transfer), and provides a prioritized set of actions to help you achieve your cyber risk outcome.
X-Analytics is a complete GRC application.
Compliance: X-Analytics includes the most popular cybersecurity frameworks (such as CIS CSC v8, NIST CSF v2.0, and CRI v2.0). You can ditch your cybersecurity framework spreadsheets. X-Analytics provides a modern web-based application where more than one person at a time can update their section of a framework, where you can invite collaborators, and where you can instantly see the results of your framework updates upon each "save and submit".
Risk: X-Analytics is a risk management application that automatically combines your compliance profile (or cyber maturity) to your threat and exposure profiles to determine your cyber risk condition. X-Analytics is complete with trending to help you understand if your cyber risk condition it getting better or worse over time. Additionally, X-Analytics provides a set of prioritized actions to help you achieve your risk management targets.
Governance: X-Analytics includes a governance module, that extends beyond the Govern function in NIST CSF 2.0, to help you undertand if the right roles, responsibilities, and practices wrap around your risk management strategy. The governance module includes a dynamic cyber governance score that aggregates your Govern function implementation, your governance rigor, and your overall cyber risk management effectiveness. Additionally, the governance module is complete with an X-Analytics Board Reporting Service (please see here).
How Can X-Analytics Help with the 9 Ways CSOs Lose Their Jobs?
X-Analytics is a cyber risk management application that was designd to help CSOs achieve optimal success. So, let's dig into the 9 ways CSOs lose their jobs.
1. Overconfidence:
In the article, the author writes:
Hubris can result in early career destruction, particularly when unproven yet popular security solutions are deployed.
The days of the loudest or most arrogant person in the room is growing old. There is a shift from subjective to objective, and X-Analytics provides an objective analysis of your cyber risk condition. The X-Analytics analysis is not loaded with bias. It is purely a combination of your unique business profile, your threat profile, your cyber maturity, and the current cyber macroeconomic condition.

In other words, the results are what they are. As a new CSO, you can use X-Analytics to set a baseline in which to communicate and develop your risk management plan. As an existing CSO, you can use X-Analytics to level the playing field, reset expectations, and develop a revised risk management plan.
There is safety in objectivity and objectivity helps to reduce complacency.
2. Promoting Runaway Complexity:
In the article, the author writes:
The challenge posed by complexity is that it adds cost at a time where cyber budgets are falling under increasing scrutiny, and it can make an organization’s cyber defenses weaker.
Three things remain true for all organizations. Your cybersecurity program is only as good as your weakest link, cybersecurity is always a cost to the business, and you can easily be distracted by emerging technologies and threats.
X-Analytics can help you identify your weakest links, it can help you control your costs, and it can help rationalize emerging technologies and threats.

X-Analytics has a broad set of insights and tools to ensure that you don't have a false sense of security, to help you analyze the benefit of new technologies before deployment, and to help you identify and address gaps before an adverse condition impacts your organizations.
X-Analytics simplifies cyber risk management.
3. Shortchanging GRC:
In the article, the author writes:
Deploying a cybersecurity stack without including a formal governance risk and compliance (GRC) program can easily upend a career.
Governance, risk, and compliance (GRC) provides balance to your risk management strategy. Since X-Analytics is a complete GRC application, X-Analytics will help you:
control costs and prevent overspend on technology,
reduce a false sense of security by providing objective results,
identify critical components within your cyber risk condition,
align your cyber risk condition and strategy with other parts of the business.
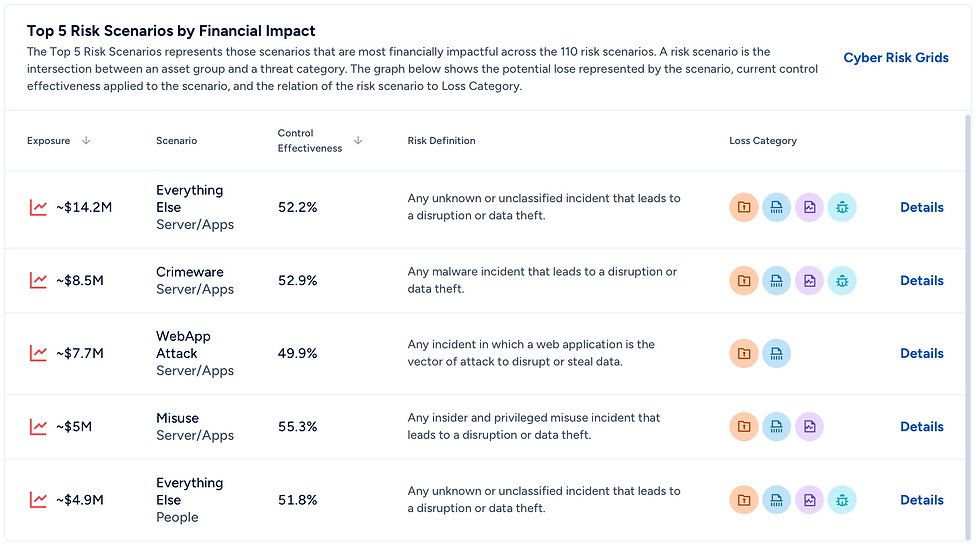
Unlike most other cyber risk management solutions, X-Analytics includes a governance module, that extends beyond the Govern function in NIST CSF 2.0, to help you undertand if the right roles, responsibilities, and practices wrap around your risk management strategy.
4. Failing to Align Cybersecurity with Enterprise Objectives:
In the article, the author writes:
Cybersecurity exists, and should be executed, within the context of the enterprise’s mission, goals, and objectives.
In today's world, most executive leaders need the CSO to frame their cybersecurity program in relation to the organization. To make this happen, the CSO needs to truly understand their organization, the CSO needs a way to compare cyber risk with other operational risks, and the CSO needs a plan that prioritizes actions that are valuable to the organization.
X-Analytics helps you provide organizational and business context by expressing your cyber risk condition as a percent of annual revenue. This normalizing technique allows you to compare your cyber risk condition with other operational risks.

Additionally, X-Analytics gives you the ability to set targets that align to your organization's risk tolerance. If you are not meeting a particular target, then X-Analytics provides prioritized guidance to help you aim your actions. Your actions ensure you get the most out of your investments, you optimize resource allocation, and you achieve your desired outcomes.
5. Underemphasizing Access Controls:
In the article, the author writes:
Enterprises often fail to adequately manage the access permissions for former employees and contractors resulting in orphan accounts that can be exploited by threat actors.
There is more than enough evidence that access control and account management are essential to any cyber risk management plan. Every major cybersecurity framework highlights the values of these controls to help reduce insider and privileged misuse, web application attacks, point-of-sale intrusion, ransomware, and many other attacks patterns.
X-Analytics provides a variety of insights to ensure you don't overlook the effectiveness of access control or account management. In almost every active X-Analytics account, access control and account management are listed within the "Top 5 Control Areas to Reduce Cyber Exposure".

X-Analytics further divides access control and account management into prioritized actions, such as:
Unique passwords and multi-factor authentication
Centralized account management and access control
Managing default accounts and disabling dormant accounts
Inventory of accounts and authentication systems
Role-based access control, granting access, and revoking access
Unlike most other risk management and GRC solutions, X-Analytics determines your "insider and privileged misuse" risk condition to help reduce your risk associated with overprivileged accounts.
6. Ignoring the Human Factor:
In the article, the author quotes Dan Lohrmann (field CISO at IT consulting firm Presidio):
The biggest mistake security leaders make is focusing entirely on technical solutions and processes. The biggest vulnerabilities come from the people side. Security experts who underestimate relationships will fail.
The largest IT outage, in IT history, was caused by human error. From Crowdstrike, to Colonial Pipeline, to thousands of other cyber incidents, the human factor was a key component.
X-Analytics was designed to account for the human factor. Specifically, it was designed to account for insider and privileged misuse, miscellaneous error, physical theft and loss, social engineering, and many other multistep incidents that exploit employees, contractors, and customers.

X-Analytics helps you understand the risk associated with the human factor, and X-Analytics helps you prioritize actions related to improving human factor risks.
Additionally, X-Analytics simplifies cyber risk management to help prevent burnout.
7. Allowing Abandoned Data to Linger:
In the article, the author writes:
Stale data in cloud-based storage may be hidden and forgotten, but it can come back without warning to wreck a CSO’s career.
Even though data breach has been the primary cyber risk theme for 20 years, data breaches still continue to happen. Part of the problem is related to cyber maturity, and part of the problem is related to data inventory, data classification, and data access management. Stale and forgotten data is lingering across thousands of organizations, which is further extended across millions of devices.
X-Analytics determines your data breach exposure and prioritizes actions to improve that exposure. Additionally, X-Analytics gives you the ability to understand how a massive data purge could improve your overall cyber risk condition.

It is important to note that a significant portion of ransomware incidents still include a data hostage element.
8. Not Building a Bridge to the Business:
In the article, the author quotes Jeff Orr (Director of Research at global technology research and advisory firm ISG's Ventana):
Ineffective communication with nontechnical stakeholders can lead to misunderstandings and confusion, sowing distrust, lack of support for security initiatives, and growing challenges when seeking security budget approvals.
As a CSO, you know the importance of effective communication with the board of directors and the executive leadership team. Unfortuntely, the cybersecurity industry has not made this easy for you. Almost every vendor, consulting firm, and technology provider serves up metrics and insights that don't translate well outside of the cybersecurity industry.
From the very beginning, we knew that X-Analytics had to help solve this problem. This is why X-Analytics determines a financial impact and probability across mutliple loss categories. The aggregation of all possible impacts, each mulitplied by the probabilty of impact, is your total cyber exposure value. This value can be used to:
Better understand your cyber risk condition
Compare your cyber risk with other operational risks
Prioritize mitigation and transfer actions
Determine return on investment for inflight and future cybersecurity project
Effectively communicate your cyber risk plan

X-Analytics provides insights to help you before and after a cyber incident.
9. Complacency:
In the article, the author writes:
The biggest career-crippling mistake is believing that everything is under control.
As a CSO, it is easy to become complacent. Many aspects of cyber risk management are complicated, you partially own the problem with others that may not care as much as you do, your budget is regularly being scrutinized, the cyber risk landscape is constantly shifting on you, and regulators and auditors just care about compliance.
X-Analytics proves that:
Everything is not under control and that all organizations have leftover risk.
Certifications and regulatory guidelines are only part of the solution and not the entire solution.
Changes in threat, exposure, and the cyber macroeconomic condition alter your cyber risk condition.
Cyber insurance is never full cost replacement.
Cyber risk management plans get stale and need to be revised to best reduce risk.

X-Analytics shows that even customers with low exposure may have severe impacts due to cyber incidents. There is always a chance that bad things happen to good companies.
Next Steps
If you are not an existing X-Analytics customer, please work with one of our amazing Account Managers to determine which X-Analytics solution is best for you.
If you are an active X-Analytics customer, please work with your Customer Success Team to best leverage X-Analytics for you cyber risk management use case.
Comments